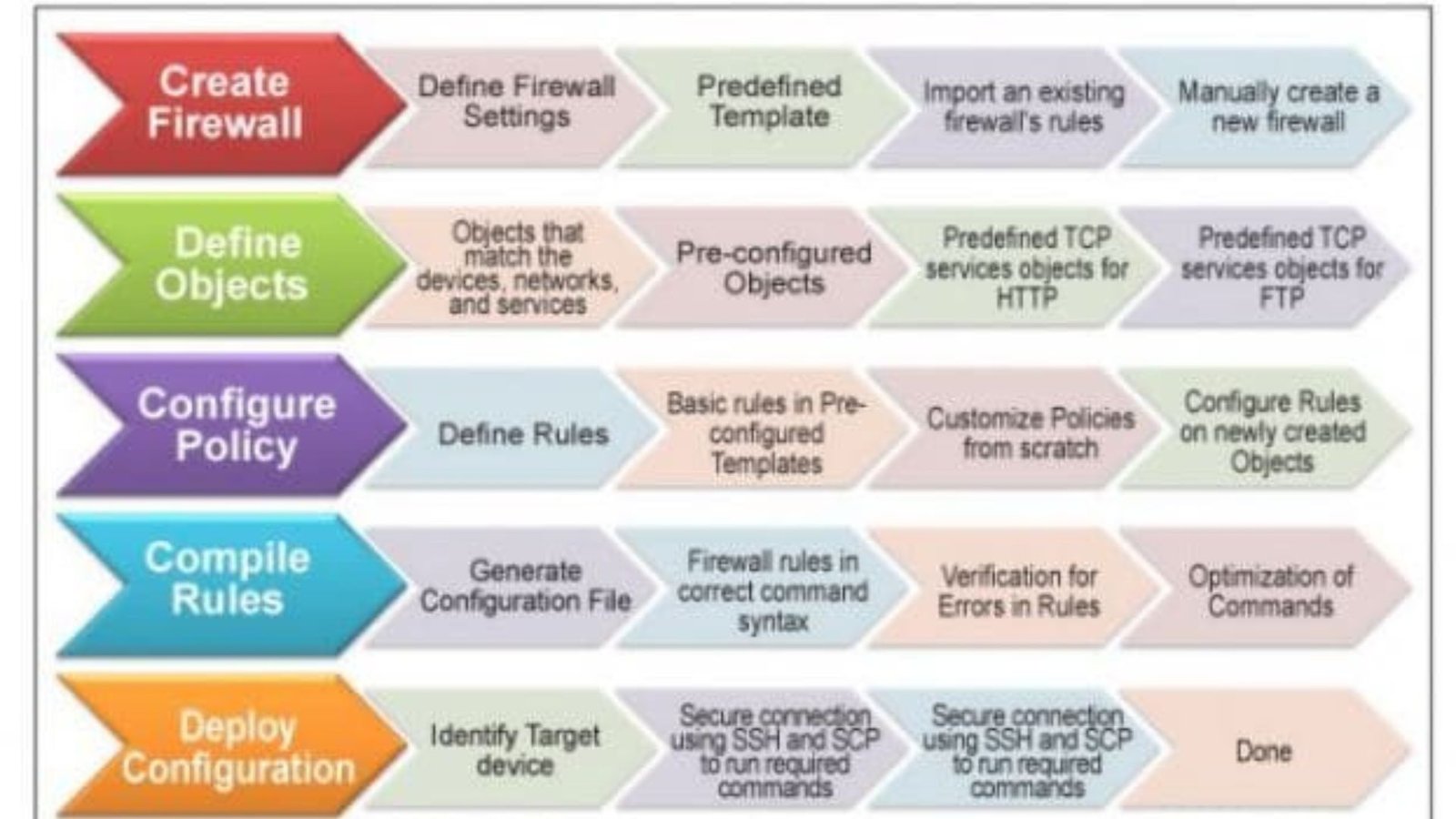
Configuring firewall settings is essential for safeguarding your computer and network from unauthorized access and cyber threats. Whether you’re setting up a new firewall or tweaking your existing configuration, understanding the right steps can help ensure robust protection for your data.
Why Configuring Firewall Settings is Important
When it comes to configuring firewall settings, the main goal is to create a barrier between your internal network and external threats. A properly configured firewall can block harmful traffic, prevent unauthorized access, and protect your sensitive information. Without effective firewall settings, your system may be vulnerable to attacks and data breaches.

Choosing the Right Firewall
Before you start configuring firewall settings, ensure you have the right firewall for your needs. There are two main types: software firewalls and hardware firewalls. Software firewalls are installed on individual devices, while hardware firewalls are standalone devices that protect entire networks. Choose the one that fits your setup, considering factors such as the size of your network and the types of threats you want to defend against.
Accessing Firewall Settings
To begin configuring firewall settings, you need to access the firewall interface. For software firewalls, this usually involves opening the program on your computer. For hardware firewalls, you may need to log in through a web browser using the device’s IP address. Ensure you have the necessary administrator privileges to make changes to the settings.
Creating and Managing Rules
One crucial aspect of configuring firewall settings is creating and managing rules. Rules define what traffic is allowed or blocked based on criteria such as IP address, port number, and protocol. Start by setting up basic rules to allow legitimate traffic while blocking known threats. You can adjust these rules as needed based on your network’s activity and security requirements.
Blocking and Allowing Applications
Another key step in configuring firewall settings is managing application permissions. Most firewalls allow you to specify which applications are permitted to access the network. Ensure that only trusted applications are allowed, and block any that could pose a security risk. Regularly review and update these permissions to reflect any changes in your software usage.
Configuring Port Settings
When configuring firewall settings, you may need to open or close specific ports to enable or restrict traffic. For example, if you’re running a web server, you’ll need to open port 80 for HTTP traffic. Conversely, close unused ports to reduce potential vulnerabilities.
Enabling Logging and Monitoring
For effective security management, enable logging and monitoring features in your firewall settings. This allows you to track and review network activity, identify potential threats, and respond to suspicious behavior. Regularly check the logs to stay informed about any unusual activity and adjust your firewall rules accordingly.
Updating Firewall Software
Configuring firewall settings is not a one-time task. Firewall software often receives updates to address new vulnerabilities and improve functionality. Regularly update your firewall software to ensure you’re protected against the latest threats. Enable automatic updates if available, or manually check for updates periodically.
Testing Your Firewall Configuration
After setting up your firewall, it’s important to test the configuration to ensure it’s working as expected. Use online tools or software designed to scan for open ports and test firewall rules. This helps verify that your firewall is blocking unwanted traffic while allowing legitimate connections.
Managing Remote Access
If you need to allow remote access to your network, configure your firewall settings to handle this securely. Set up VPNs (Virtual Private Networks) or secure remote desktop connections to ensure that remote access is encrypted and protected. Be cautious about allowing remote access and ensure it’s only available to authorized users.
Understanding Advanced Settings
For advanced users, many firewalls offer additional settings, such as intrusion detection systems (IDS) and intrusion prevention systems (IPS). These features can provide an extra layer of security by identifying and preventing suspicious activity. Familiarize yourself with these advanced settings if you require enhanced protection.
Educating Users
Proper education of users within your network is also crucial when configuring firewall settings. Ensure that everyone understands the importance of security practices, such as avoiding suspicious links and not downloading unverified software. A well-informed user base can help prevent security breaches that could compromise your firewall’s effectiveness.
Conclusion
Configuring firewall settings is a crucial step in protecting your computer and network from cyber threats. By selecting the right firewall, managing rules and permissions, and regularly updating and reviewing your settings, you can create a robust defense against unauthorized access and attacks. Follow these steps to ensure your firewall provides effective and reliable security for your digital environment.